Cyber Security
Is your business secure?
Organisations need to take proactive steps to enhance their security posture and better protect their data and assets from cyber threats. In a hypercompetitive business environment, organisations simply cannot afford cyber related outages coupled with the reputation issues that arise from cyber related incidents.

Overview
Avoid security breaches, data loss & downtime
BAMITS provides clients with critical cyber security services that provide protection against cyber threats. Our services include a range of measures designed to prevent, detect and respond to cyber-attacks, as well as ongoing monitoring and risk management. We take a holistic approach to cyber security management. Our services focus on network security, cloud security, endpoint security and identity and access management.
IT security isn’t a luxury, it’s necessity
By working with BAMITS, our clients are able to benefit from our expertise and proven delivery process. We’re able to provide ongoing support, monitoring and updates to ensure our clients remain protected against the latest threats. Our services aim to minimise the risk of data breaches, cyber-attacks and other security incidents, allowing our clients to focus on their core business activities with peace of mind.
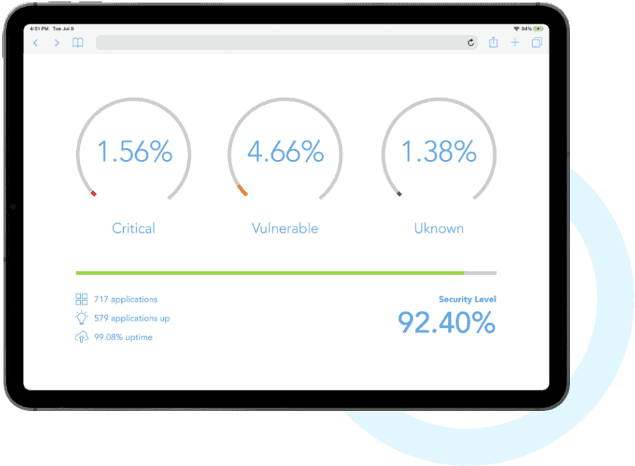
Security Audit
Baseline analysis
An all-encompassing approach to IT security. BAMITS will conduct a range of activities, from reviewing documentation, interviewing staff, and analyzing systems and data flows. In addition, we will use tools and techniques such as vulnerability scanning, penetration testing, and security assessments to identify potential risks and vulnerabilities.
Subject to the findings, we will work with our clients to implement a number of changes such as implementing additional security controls or improving existing processes and policies.

Authentication and Authorization Weaknesses,

Absence of Data Encryption,

OS Command and SQL Injection Flaws,

Software Bugs and Vulnerabilities,

Weak Passwords,

Lack of Integrity Checks,

URL Redirection Vulnerabilities,

Trust Issues with the Website or Application,
Training
Intrusion detection and prevention
Training is an important aspect of protecting against cyber threats. BAMITS focuses on training sessions that highlights intrusion detection and prevention methods that help our clients improve their ability to identify and respond to potential security breaches. Our services implement tools such as firewalls, intrusion detection system and antivirus software, as well as establishing processes and procedures for monitoring and responding to potential threats.
Our training services are customised based on the client requirement and the security services that the clients have engaged us to provide. We delivery training to our clients via a range of formats such as classroom training, ongoing courses or hands-on workshops.

Detect social engineering,

Remote file inclusions and malware injections,

SQL injections used to access databases,
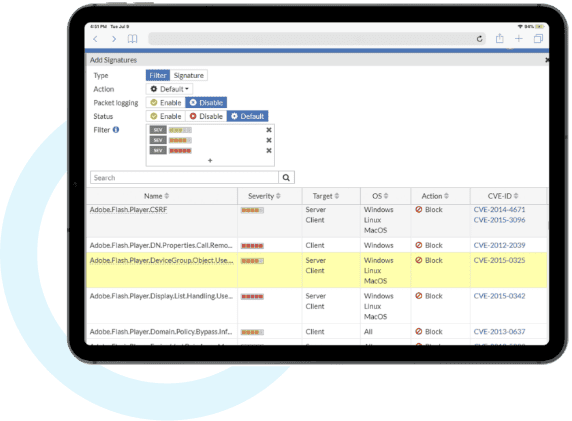
IT Security Assessment
By having BAMITS undertake a security assessment, our clients benefit from our experienced security professionals who have a deep understanding of the latest threats and trends in the IT security landscape. Our service can help organisations identify and address potential vulnerabilities and risks before they can be exploited by cybercriminals, helping to minimize the risk of data breaches and other security incidents. A BAMITS security assessment is a critical tool for companies looking to ensure the security and integrity of their IT systems and infrastructure.
Our Services Include:
Device Management
Securing and maintaining devices such as computers, mobile devices, and other endpoints within your infrastructure. This includes activities such as installing and updating software, managing user permissions and access, enforcing security policies, and monitoring devices for potential security breaches or vulnerabilities.
Network & Cloud-Based IT Security
Securing our clients network and cloud infrastructure, including routers, switches, firewalls, and cloud-based services, such as software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS).
Threat Intelligence & Predictive Analytics
Proactively identify and mitigate potential security threats through the collection and analysis of data from to identify emerging threats and trends. Coupled with data analytics and machine learning to forecast potential threats and identify patterns that may indicate a potential security breach.
Incident Response and Recovery
Identifying the nature and scope of the incident, containing the incident to prevent further damage, and implementing measures to remediate the incident and restore normal operations. Recovery involves restoring affected systems and data to their pre-incident state, as well as implementing measures to prevent future incidents.
IT Risk Assessments
Assessing the likelihood and impact of various risks, such as cyber-attacks, data breaches, and system failures, and developing strategies to mitigate these risks. We undertake a comprehensive review of your IT systems, policies, and procedures, as well as a detailed analysis of potential threats and vulnerabilities.
Ransomware Protection Suite
The implementation of a range of security controls, such as anti-malware tools, firewalls, and intrusion detection and prevention systems, as well as measures for backing up and restoring data. Ransomware protection suite can help to prevent these attacks by detecting and blocking malicious activity, as well as providing backup and recovery options in the event of an attack.
Reduce your time to detection and protect your
business in real time.
Utilise our expertise, have BAMITS provide a high level of protection against cyber threats. Our team uses the latest security tools, technologies, and best practices, and can help your organisation stay up to date on emerging threats and trends.
We can provide round-the-clock monitoring and support for IT systems and data, helping your organisation identify and respond to security incidents in real-time, mimimising the impact of potential breaches or attacks.
Find managed IT security services that fit you
Contact our support team today for an initial free cyber security consultation.

